Every week we share trending articles and tools in our newsletter. More than 10,000 people enjoy reading, and you will love it too. The only way ive been able to get rid of SearchAssist.net is by removing it from the registry and every file on hdd that had it. The WinUtilities works on 32-bit and 64-bit versions of Windows XP and Windows 7, 8, 10. I have Special Offer Notifications Off as I also have Norton Tune Up features Off.
Or you could bite the bullet and buy the missus a new computer to replace that relic, since she’s already backed up the embroidery files that are its primary mission. While installing service pack 3 on my dell x300 laptop it crashed. I can’t get my wireless card or my SD card reader to work. So far I have not experienced any problems myself, but then I have installed the whole system myself, ensuring the correct drivers etc. (partly thanks to PC Pitstop’s Driver click this Alert).
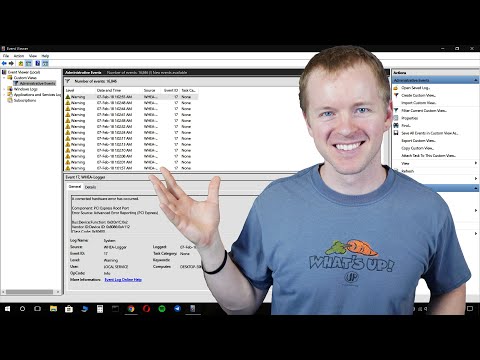
This could be due to someone trying to hack into a system. However, it could also mean someone forgot his or her password, the account had expired, or an application was configured with the wrong password. These events include the following pieces of information. The most common reason people look at Windows logs is to troubleshoot a problem with their systems or applications. Now that the box has appeared in your screen window click the downward arrow next to Logged to select a time range.
How to Change Brightness in Windows 11
From there, you should open your favorite search engine and look up your error message. Don’t stop on the first hit you find for your error, even if it looks like the person in the newsgroup solved their problem. Continue looking through the other references to ensure that the problem they had is the same one you did, or that the KB article is for the version and service pack you have. You can generally trust many Microsoft posts, and those from the “MVP’s” Microsoft’s Most Valuable Professional champions. They will normally display an “MVP” badge on their sites, they post frequent blogs, and you’ll see them in many of the Forums.
For example, we covered how to check your SSL certificate as a website owner and how to clear your browsing data cache to fix this issue as a visitor. From there, search for the “Allow invalid certificates for resources loaded from localhost” option and select Enabled. Bypassing the privacy error manually only fixes the issue temporarily.
- A few names of the categories lined up here read as font locations, menu order, shared folders, uninstall locations and shared dlls.
- Unsurprisingly, such a powerful operating system necessitates the use of appropriate hardware.
- The registry cleaner in this program has a regular and deep scanning option to ensure it gets as many errors and problems as it can.
- You can also disable writing any errors to the Application EventLog.
If it detects any , Windows will repair and replace the files, ensuring the overall integrity of your Windows installation. For AlwaysUp, events from your application named “My Application” will be logged with Source set to My Application . The Event Log Messages Page lists and explains the events reported.
Solution or Workaround
After doing that, try to synchronize your clock again. Before trying this solution it’s recommended to back up your registry in case anything goes wrong. Modify any settings easily with these software tools. Set the Startup Type to Automatic and start the service again. Click Apply and OK to save changes and restart your computer. Before trying this solution, make sure that Windows Time service is set to Automatic and running.
How Do I Detect Registry Errors?
Monitoring combined with logging gives administrators and developers immediate attention to a problem and helps them find it more quickly. Debugging involves research and analysis, so even just a line in a log file might not be enough for a developer to understand the problem. More research into previous events might be needed, so the ability to search logs is also necessary. Your logs could be thousands of line items, so the ability to search makes debugging and root cause analysis much faster and more efficient.
